





Attackers and malware will always be trying to reverse engineer published apps to find a breach. Research by the Talsec Security Lab team has detected reverse engineering and tampering attempts within a very short time after the launch of apps that deal with sensitive user data and payments.
The Talsec team can catch and investigate such attack attempts on the apps equipped with Talsec App self-protection and online monitoring SDK
Attackers and malware will always be trying to reverse engineer published apps to find a breach. Research by the Talsec Security Lab team has detected reverse engineering and tampering attempts within a very short time after the launch of apps that deal with sensitive user data and payments.
Threat modelling
Penetration testing
Ethical hacking


complete picture about app security level, vulnerabilities, and obtain guidelines on how to fix the security flaws
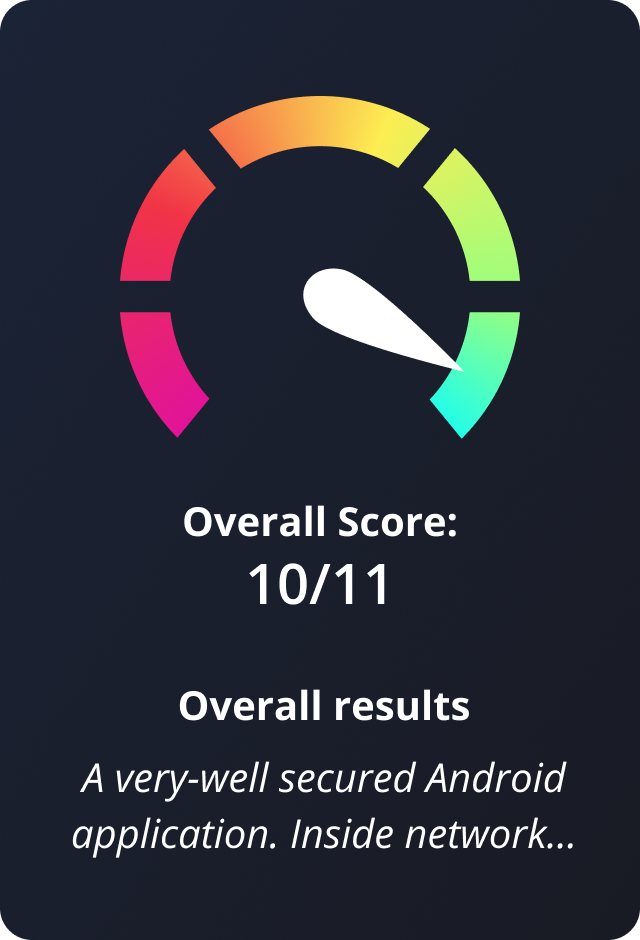
Get a complete picture about app security level, vulnerabilities, and obtain guidelines on how to fix the security flaws


Apply attack methods to verify exploitability of discoveries
With Talsec every app owner can secure mobile applications and protect their users in the most cost-effective way.
Get in touch