Fortify Your Mobile App for DORA Compliance with Talsec SDK
The Digital Operational Resilience Act (DORA), represents a paradigm shift for the EU's financial sector.

It’s no longer enough to have robust backend and network security; DORA mandates a comprehensive, end-to-end approach to digital resilience.
For mobile developers and financial institutions, this puts the spotlight squarely on a critical, often-underestimated attack surface: the mobile application itself. As the primary interface for millions of customers, your mobile app is now a key component of your regulatory compliance strategy.
Understanding DORA's Core Mandates
DORA is built on several key pillars, but for mobile app security, two are particularly paramount:

ICT Risk Management
Financial entities must establish a comprehensive framework to identify, protect, detect, respond to, and recover from ICT-related risks. This includes continuous monitoring and protection of software and systems.

ICT Third-Party Risk Management
The regulation scrutinizes the entire digital supply chain. If you integrate a third-party SDK - like one for analytics, advertising, or security - you are responsible for ensuring it doesn’t introduce new vulnerabilities. Your third-party solutions must be as resilient as your own systems.
The Mobile Blind Spot: Why Client-Side Security is Crucial for DORA
While servers are locked down in secure data centers, your mobile app runs in the wild, on untrusted user devices. This environment is ripe for attacks that DORA aims to prevent. Threats like reverse engineering to steal API keys, app tampering or repackaging to inject malware, and overlay attacks to steal credentials can all lead to significant data breaches or service disruptions. Under DORA, such an event would be classified as a major ICT-related incident, requiring mandatory reporting to authorities and triggering potential penalties.
Bridging the Compliance Gap with Talsec
This is where a specialized mobile security SDK like Talsec becomes a compliance accelerator. Talsec is a Runtime Application Self-Protection (RASP) and mobile API protection solution that directly addresses DORA's requirements on the client side.
Meeting ICT Risk Management (Article 9):
Talsec’s multi-layered defense helps you identify and protect. It detects high-risk environments by checking for root/jailbreak status, emulators, and attached debuggers. Its RASP capabilities prevent runtime threats like tampering and repackaging, ensuring your app's integrity and protecting the sensitive logic and keys within.
Talsec’s multi-layered defense helps you identify and protect. It detects high-risk environments by checking for root/jailbreak status, emulators, and attached debuggers. Its RASP capabilities prevent runtime threats like tampering and repackaging, ensuring your app's integrity and protecting the sensitive logic and keys within.
Enhancing Incident Detection (Article 17):
DORA requires timely incident detection and response. Talsec's security event monitoring is a crucial tool here.
DORA requires timely incident detection and response. Talsec's security event monitoring is a crucial tool here.
Whenever a threat is detected on the client-side—from a repackaged app trying to communicate with your backend to an attempt to a remote access tool being deployed in a sophisticated social engineering attack—Talsec sends an immediate, detailed alert to your Security Operations Center (SOC) or SIEM via a configurable webhook. This provides the real-time visibility needed to respond before an incident escalates.
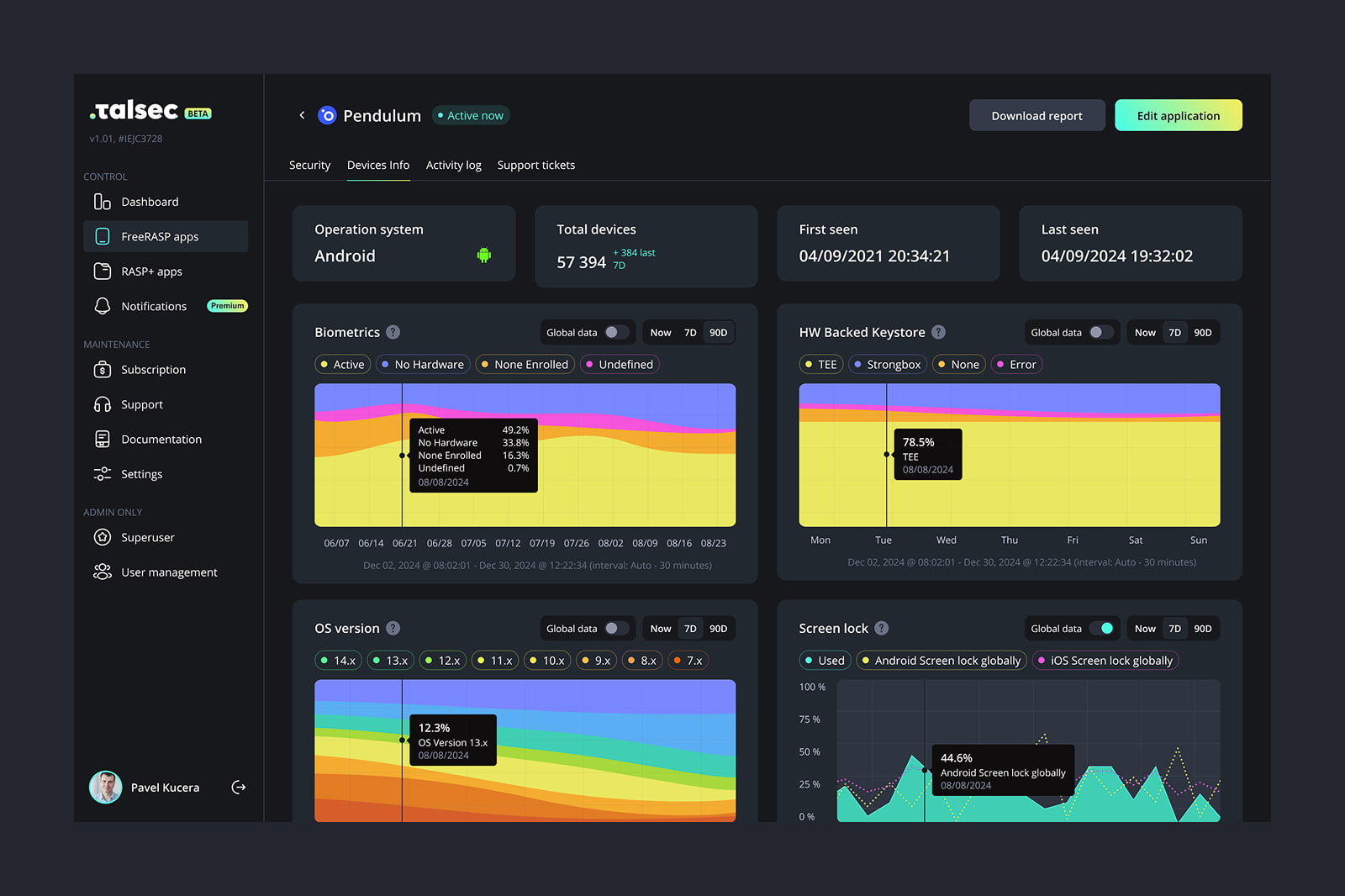
Additionally Talsec’s Portal now provides Real-Time Threat Monitoring, allowing you to gain immediate and continuous insight into the security events affecting your application. Intuitive dashboard allows you to track the count, type, and frequency of threats over time, including critical intentional attacks like tampering, reverse-engineering (debugging and hooks), and emulator usage. You can identify anomalies as they happen and respond before they escalate into major incidents. Portal allows you to investigate specific security events with granular detail. Filter data by app version, operating system, device type, and geographic location. Understand exactly which parts of your user base are being targeted and how, enabling a precise and effective response.
Strengthening Third-Party Risk Management (Article 28):
By integrating Talsec, you are adopting a security-focused, resilient third-party solution. Talsec helps you demonstrate due diligence by hardening your application against common attack vectors, providing a verifiable layer of security that strengthens your overall DORA compliance posture.
By integrating Talsec, you are adopting a security-focused, resilient third-party solution. Talsec helps you demonstrate due diligence by hardening your application against common attack vectors, providing a verifiable layer of security that strengthens your overall DORA compliance posture.
A Practical Scenario: Talsec in Action
Imagine an attacker loads your financial app onto an emulator and attaches a debugger to analyze its network requests and extract API keys. Without protection, this is a trivial task. With Talsec integrated, the SDK immediately detects the debugger and the unsafe emulator environment. It can be configured to instantly terminate the app, preventing the attack. Simultaneously, it sends a security event about the detected debugger and related app and device security relevant data to your monitoring dashboard that can be tied to the attacker's account, instance ID, or session ID, allowing for easier tracking across all your systems. Your security team is now aware of the attempt, the device fingerprint, and can take proactive measures, all in line with DORA's 'detect and respond' principles.
Conclusion: From Regulatory Burden to Resilient Architecture
DORA should not be viewed as merely a compliance hurdle, but as a directive to build genuinely resilient digital services. True operational resilience is impossible if the mobile client remains a soft target. By embedding advanced client-side protection with a solution like Talsec, businesses can effectively address key DORA requirements, turning a regulatory mandate into a strategic advantage that enhances security, protects data, and builds customer trust in an increasingly hostile digital world.
To fully appreciate how an in-app security SDK helps meet DORA's stringent requirements, let's break down how Talsec's core technologies map directly to the regulation's principles of protection, detection, and resilience.

Runtime Application Self-Protection (RASP)
What it is:
A dynamic security layer that monitors the application and its environment while it is running.
How it helps with DORA:
Addresses "Detect and Respond" (Article 17):
RASP is the first line of defense against active attacks. It detects real-time threats like attached debuggers (preventing runtime manipulation), hooking frameworks like Frida (stopping dynamic analysis), and execution on emulators or rooted/jailbroken devices. Upon detection, it can trigger a response—from terminating the app to sending an immediate alert—directly fulfilling DORA's mandate for active incident detection and response capabilities.
RASP is the first line of defense against active attacks. It detects real-time threats like attached debuggers (preventing runtime manipulation), hooking frameworks like Frida (stopping dynamic analysis), and execution on emulators or rooted/jailbroken devices. Upon detection, it can trigger a response—from terminating the app to sending an immediate alert—directly fulfilling DORA's mandate for active incident detection and response capabilities.
Provides Data for Incident Reporting:
The security events generated by RASP provide the precise, actionable data required for the "major ICT-related incident" reports mandated by DORA. Our comprehensive data provide a detailed and multi-faceted view of each device, encompassing granular device information (model and OS), a thorough security posture assessment (screen lock, biometrics, hardware keychain, and OS integrity), and specific application insights (certificate hash and installation source), along with a vigilant log of detected security incidents (rooting, jailbreaking, Frida, VPN usage, and various attacks).
The security events generated by RASP provide the precise, actionable data required for the "major ICT-related incident" reports mandated by DORA. Our comprehensive data provide a detailed and multi-faceted view of each device, encompassing granular device information (model and OS), a thorough security posture assessment (screen lock, biometrics, hardware keychain, and OS integrity), and specific application insights (certificate hash and installation source), along with a vigilant log of detected security incidents (rooting, jailbreaking, Frida, VPN usage, and various attacks).

AppHardening
What it is:
A suite of static protection techniques applied to the app's code before it is released.
How it helps with DORA:
Fulfills the "Protect" Function (Article 9):
AppHardening focuses on prevention. By using Dynamic TLS Pinning, control of obfuscation usage and string encryption, it makes it exceptionally difficult for attackers to reverse-engineer your application. This protects sensitive information embedded within the app, such as API keys, secret algorithms, and business logic.
AppHardening focuses on prevention. By using Dynamic TLS Pinning, control of obfuscation usage and string encryption, it makes it exceptionally difficult for attackers to reverse-engineer your application. This protects sensitive information embedded within the app, such as API keys, secret algorithms, and business logic.
Strengthens the Digital Supply Chain:
A hardened app is a more resilient component in your overall ICT infrastructure. It prevents the app from becoming the weak link that exposes your backend systems to attack, thereby supporting the holistic view of risk management central to DORA.
A hardened app is a more resilient component in your overall ICT infrastructure. It prevents the app from becoming the weak link that exposes your backend systems to attack, thereby supporting the holistic view of risk management central to DORA.

Malware Detection
What it is:
An on-device threat intelligence feature that specifically looks for malicious applications and frameworks installed on the user's device.
How it helps with DORA:
Proactive ICT Risk Identification:
This feature extends protection beyond the app itself to the user's potentially compromised environment. It can identify financial malware, keyloggers, and overlay attack tools (which use fake login screens to steal credentials).
This feature extends protection beyond the app itself to the user's potentially compromised environment. It can identify financial malware, keyloggers, and overlay attack tools (which use fake login screens to steal credentials).
Prevents High-Impact Incidents:
By detecting an overlay malware before the user logs in, Talsec can prevent credential theft and subsequent fraudulent activity. This proactive step stops a potential major incident from ever occurring, which is the ultimate goal of operational resilience.
By detecting an overlay malware before the user logs in, Talsec can prevent credential theft and subsequent fraudulent activity. This proactive step stops a potential major incident from ever occurring, which is the ultimate goal of operational resilience.

AppiCrypt® (Mobile API Protection)
What it is:
A powerful cryptographic mechanism that ensures your backend API only communicates with genuine, untampered instances of your mobile app.
How it helps with DORA:
Secures the Entire ICT System:
DORA is concerned with the resilience of the entire digital operation, not just the mobile app. AppiCrypt is critical here. It uses client attestation to block unauthorized API traffic from bots, scripts, and repackaged apps. This protects your servers from API abuse, credential stuffing, and other automated attacks that could disrupt services or cause a data breach.
DORA is concerned with the resilience of the entire digital operation, not just the mobile app. AppiCrypt is critical here. It uses client attestation to block unauthorized API traffic from bots, scripts, and repackaged apps. This protects your servers from API abuse, credential stuffing, and other automated attacks that could disrupt services or cause a data breach.
Guarantees Integrity and Authenticity:
By cryptographically signing API requests, AppiCrypt provides a strong guarantee of the client's authenticity and the integrity of the data in transit. This is a cornerstone of building a resilient and trustworthy system, as mandated by DORA's risk management framework.
By cryptographically signing API requests, AppiCrypt provides a strong guarantee of the client's authenticity and the integrity of the data in transit. This is a cornerstone of building a resilient and trustworthy system, as mandated by DORA's risk management framework.





